Deploy preventive, detective, and corrective security controls to safeguard digital and physical assets.
Implement strong authentication and authorization mechanisms, such as multi-factor authentication (MFA) and role-based access control (RBAC).
Secure network infrastructure through firewalls, intrusion detection/prevention systems (IDS/IPS), and endpoint protection.
Adopt encryption technologies to protect sensitive data at rest, in transit, and in use.
Regularly test and validate security controls to ensure effectiveness.
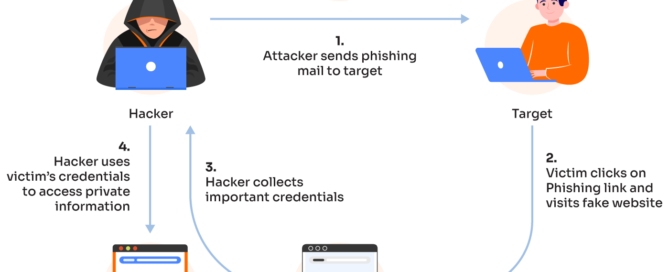
Pre-Authentication Trust Verification: A Framework for Validating the Authenticity of Websites and Applications Before Login
Abstract 🇬🇧 English Abstract Before entering a password, a user [...]