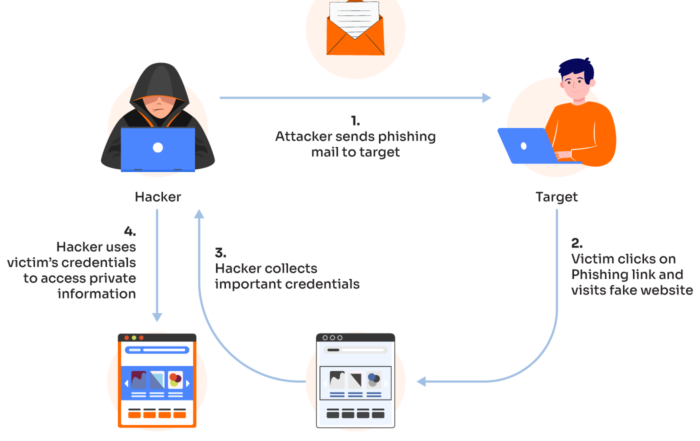
Pre-Authentication Trust Verification: A Framework for Validating the Authenticity of Websites and Applications Before Login
Abstract 🇬🇧 English Abstract Before entering a password, a user should know whether the login page or app is real. This article proposes a pre-authentication trust verification framework, where personalized markers (image, phrase, sound, or [...]
Foresight and Audit in Cloud Data Security | Prévision et audit dans la sécurité des données en nuage
Foresight and Audit in Cloud Data Security: Challenges and Strategic Imperatives Abstract The migration from physical hard drives to cloud storage has significantly reshaped the information security landscape. Traditional methods of foresight—anticipating risks [...]
Toward Intelligent and Adaptive Security Policies: The Future of AI-Driven Governance
Abstract While artificial intelligence (AI) is increasingly used to enhance information security, its full potential remains underutilized. Many leading cloud providers still rely on static security benchmarks like NIST 800-53, which, although comprehensive, do not [...]
Preparing for Ultra-Short Certificate Lifespans: Budgeting and Automation Strategies for 2026–2029
1. The Shrinking Lifespan of TLS Certificates In an effort to improve digital trust and strengthen resistance against cryptographic compromise, the CA/Browser Forum has introduced a timeline to reduce the maximum validity period of publicly [...]
Legacy Encryption and the Emerging Threat of Data Archive Exposure in the Post-Quantum Era
Introduction Data encryption has long been a cornerstone of information security, but encryption algorithms are not eternal. As computational capabilities advance—especially with the advent of quantum computing—legacy cryptographic schemes become increasingly vulnerable. The storage of [...]
The Rapid Obsolescence of TLS 1.2 Cipher Suites and the Need for AI-Driven Configuration Automation
AbstractEncryption algorithms become obsolete at a rapid pace, especially in the context of TLS (Transport Layer Security) protocols. While TLS 1.2 remains widely deployed, many of its cipher suites are now considered weak or deprecated. [...]
Stay updated with the latest trends, industry news, and expert insights in Information Security Governance and Cybersecurity.
What We Cover
🛡 Cybersecurity Trends & Threats – Analysis of the latest cyber risks and security developments.
📖 Case Studies & Insights – Real-world applications of security governance and compliance strategies.
📢 Industry News & Regulations – Updates on global cybersecurity standards and regulatory changes.
🎓 Professional Development – Tips on security certifications, training, and career growth.
🚀 Check back regularly for updates and insights from the cybersecurity world!