Abstract
Encryption algorithms become obsolete at a rapid pace, especially in the context of TLS (Transport Layer Security) protocols. While TLS 1.2 remains widely deployed, many of its cipher suites are now considered weak or deprecated. This paper examines the ongoing deprecation of specific TLS 1.2+ cipher suites, highlights the limitations of current standards such as NIST SP 800-52 Revision 2, and proposes an AI-based approach to automate configuration updates in response to evolving cryptographic threats.
1. Introduction
Cryptographic algorithms, particularly those used in widely deployed protocols like TLS, evolve rapidly in response to advances in attack techniques and cryptanalysis. While TLS 1.2 has been a staple of secure communications, several of its cipher suites are no longer considered secure due to inherent weaknesses in algorithms such as CBC (AES_128_CBC or AES_256_CBC).
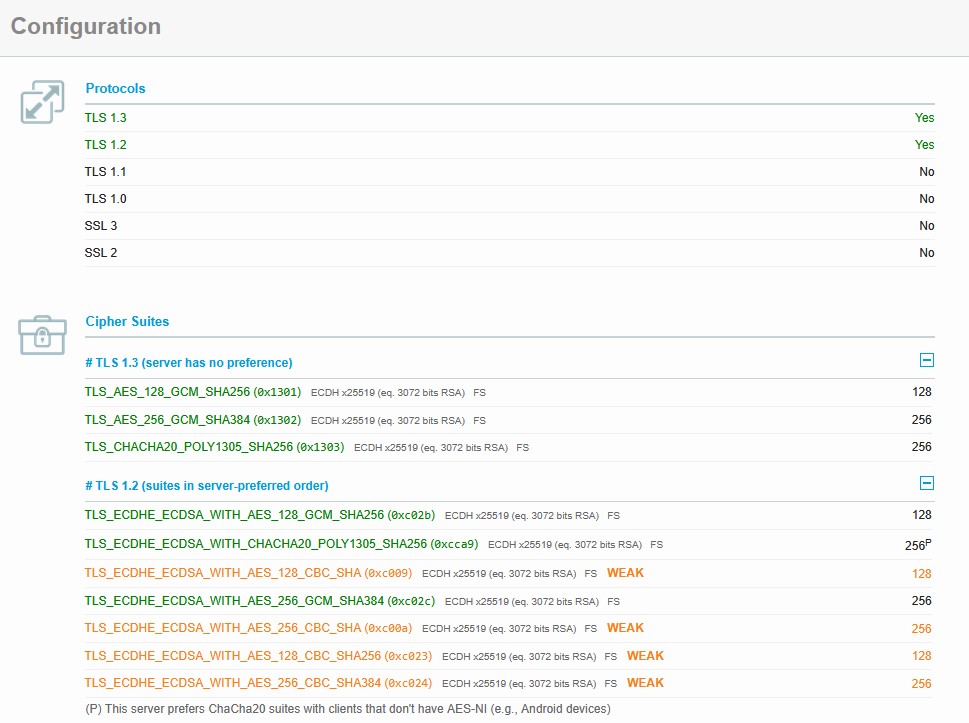
2. Deprecated TLS 1.2 Cipher Suites
Numerous organizations have begun deprecating the following TLS 1.2 cipher suites due to known vulnerabilities or weaknesses:
-
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 -
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 -
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 -
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 -
TLS_RSA_WITH_AES_128_CBC_SHA256 -
TLS_RSA_WITH_AES_128_GCM_SHA256 -
TLS_RSA_WITH_AES_256_CBC_SHA256 -
TLS_RSA_WITH_AES_256_GCM_SHA384
These suites are vulnerable to attacks such as Lucky13, BEAST, and padding oracle attacks due to the use of CBC mode and outdated hash algorithms. As a result, leading platforms and security-conscious organizations have started phasing them out (e.g., Bosch IoT, LearnUpon).
3. Limitations of Current Standards
The current U.S. government guidance on TLS usage, NIST SP 800-52 Revision 2, was published in 2019. While it was comprehensive at the time, it is no longer sufficient for today’s threat landscape. Even though updates are planned, and some documentation contains references as recent as January 2025, the standard does not address the latest deprecations and industry practices.
Other national standards, such as those published by the Canadian Centre for Cyber Security (January 2025), often refer to NIST as a foundational reference (ITSP.40.062), which further propagates outdated configurations unless updated dynamically :
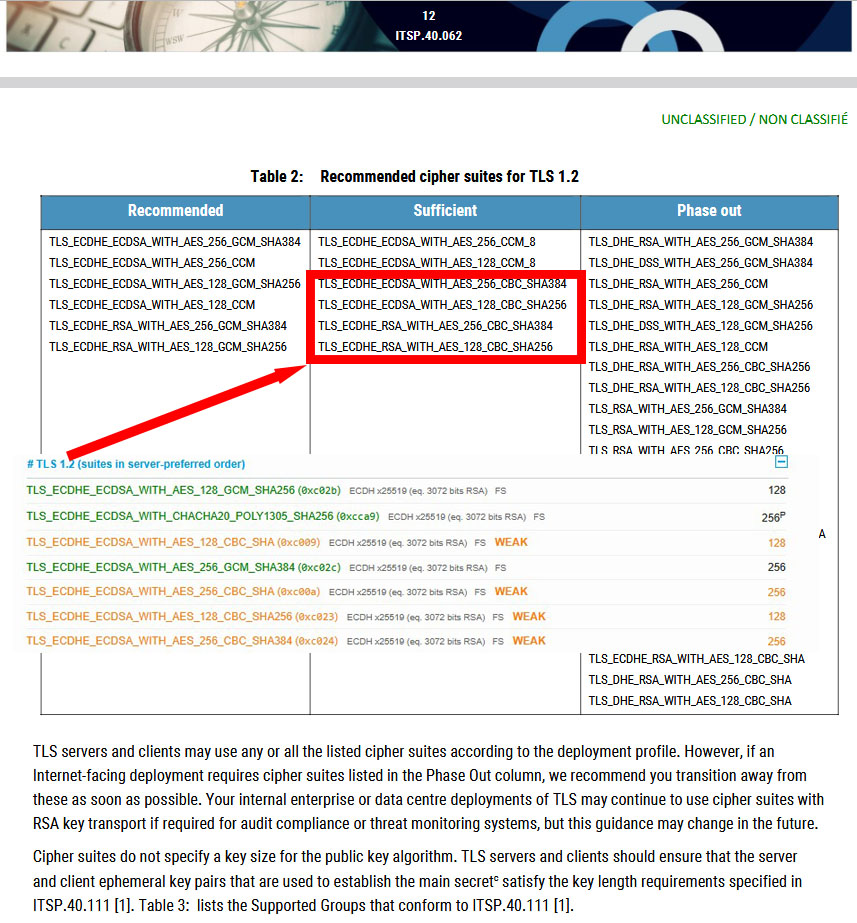
4. The Challenge of Tracking TLS Evolution
Tracking the evolving standards for TLS via resources such as the IETF’s datatracker (https://datatracker.ietf.org/doc/search?name=TLS+1.2) is an increasingly complex task due to the sheer volume and technical detail of drafts and RFCs. Manual tracking introduces delays and errors in adapting server/client configurations to the latest security guidance.
5. AI and Automation: The Future of Crypto Maintenance
To close the gap between cryptographic policy updates and their implementation in real-world systems, automation is key. Artificial intelligence and machine learning can be used to monitor sources like RFCs, CVE databases, and standards organizations, and automatically recommend or even deploy updates to server and client configurations.
In addition, national standardization bodies should provide API-accessible, automatically updated configuration tables that reflect the most current secure cipher suites and settings. This would allow security teams to dynamically apply best practices in real time.
6. Recommended Tools
A valuable resource discovered during this study is the Mozilla SSL Configuration Generator, which offers up-to-date recommendations for a wide variety of server platforms. Its regularly updated output reflects industry best practices and is highly recommended for practical use.
7. Conclusion
As encryption algorithms and cipher suites continue to age rapidly, it is no longer sufficient to rely solely on static guidance from multi-year publications. Automation and AI-based monitoring of cryptographic standards and best practices are essential for staying ahead of emerging threats. Governments and standardization bodies like NIST and the Canadian Centre for Cyber Security should offer live, API-accessible databases of recommended configurations to enable immediate adaptation across all digital infrastructure.
🔐 Official Standards and Government Publications
-
NIST (National Institute of Standards and Technology)
https://csrc.nist.gov
Source of authoritative U.S. government cryptographic standards, including: -
Canadian Centre for Cyber Security
https://www.cyber.gc.ca
National guidance on network protocol security: -
IETF (Internet Engineering Task Force) – TLS Working Group
https://datatracker.ietf.org
Tracks RFCs and drafts related to TLS protocols:
🛠️ Practical TLS Configuration Tools
-
Mozilla SSL Configuration Generator
https://ssl-config.mozilla.org
Provides up-to-date TLS configurations for various server platforms. -
OWASP Transport Layer Protection Cheat Sheet
https://cheatsheetseries.owasp.org/cheatsheets/Transport_Layer_Protection_Cheat_Sheet.html
Practical guidance on secure TLS setup. -
SSL Labs by Qualys
https://www.ssllabs.com
Online tool to analyze your website’s SSL/TLS configuration and rating.
🧪 Research Blogs and Industry Reports
-
Google Security Blog
https://security.googleblog.com
Updates on security developments, including TLS deprecations. -
Cloudflare Blog
https://blog.cloudflare.com
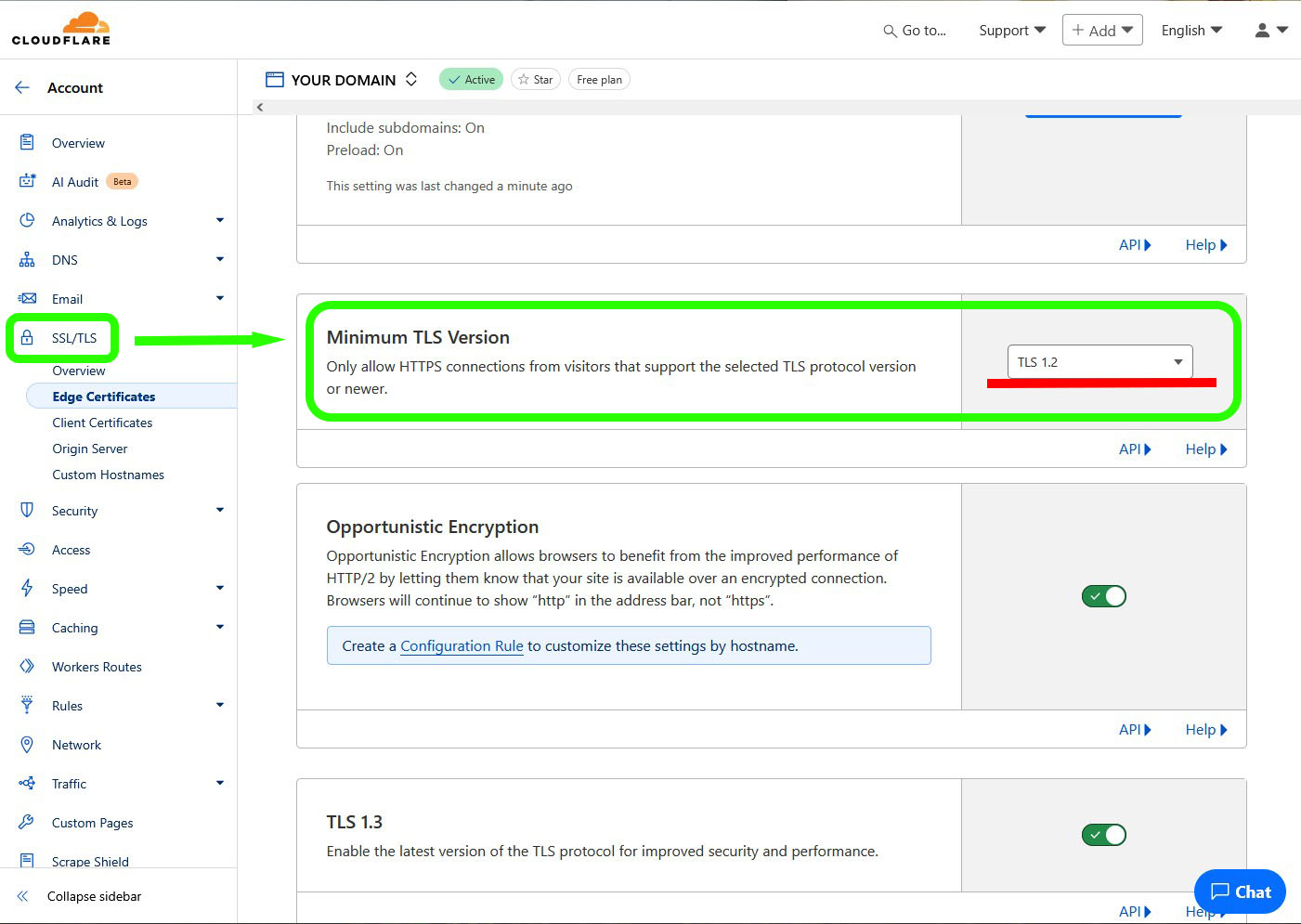
In-depth articles on TLS, HTTPS, and cryptographic protocol changes at scale. - How to Upgrade TLS 1.0 to TLS 1.2 in Cloudflare (Step-by-Step Guide):
-
Let’s Encrypt Blog
https://letsencrypt.org/blog
News and updates on TLS adoption, protocol support, and deprecation.
📊 Vulnerability Databases
-
National Vulnerability Database (NVD)
https://nvd.nist.gov
A comprehensive database of known vulnerabilities (CVEs), including those affecting TLS and its components.



Leave A Comment